SafeZone
TryHackMe Walkthrough - SafeZone
Enumeration
$ rustscan -a target | tee rust.txt
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/ehogue/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.10.240.179:22
Open 10.10.240.179:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p ")
[~] Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-09 16:34 EDT
Initiating Ping Scan at 16:34
Scanning 10.10.240.179 [2 ports]
Completed Ping Scan at 16:34, 0.23s elapsed (1 total hosts)
Initiating Connect Scan at 16:34
Scanning target (10.10.240.179) [2 ports]
Discovered open port 22/tcp on 10.10.240.179
Discovered open port 80/tcp on 10.10.240.179
Completed Connect Scan at 16:34, 0.23s elapsed (2 total ports)
Nmap scan report for target (10.10.240.179)
Host is up, received syn-ack (0.23s latency).
Scanned at 2021-07-09 16:34:23 EDT for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.56 secondsWeb Site

I have something to tell you , it’s about LFI or is it RCE or something else?
Admin Access
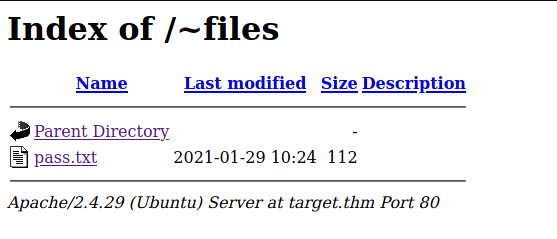
Getting a Shell
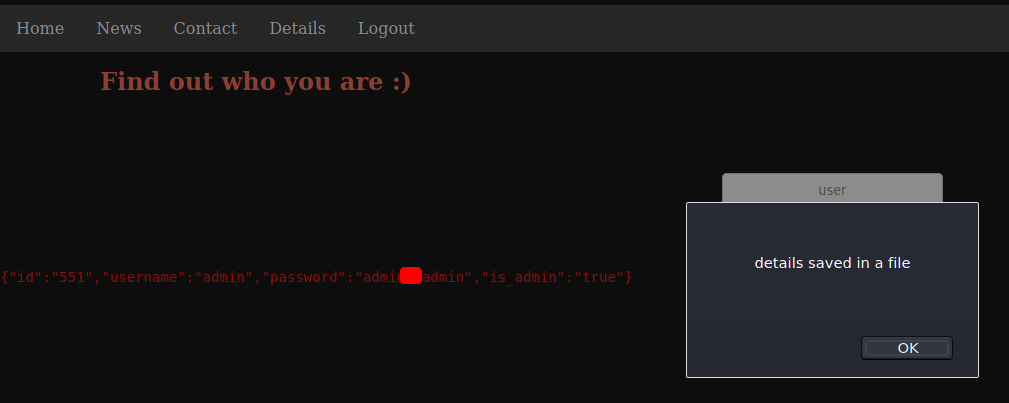
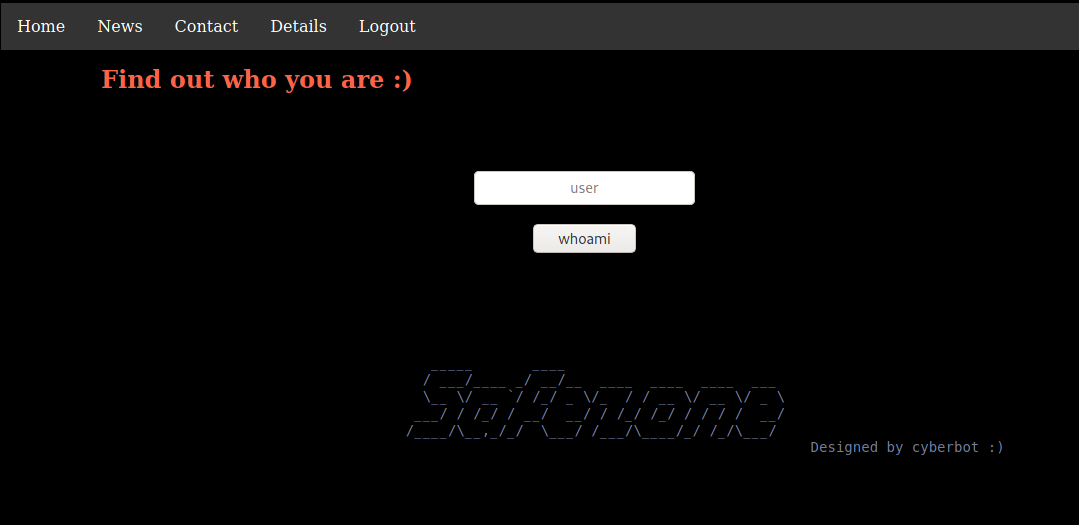
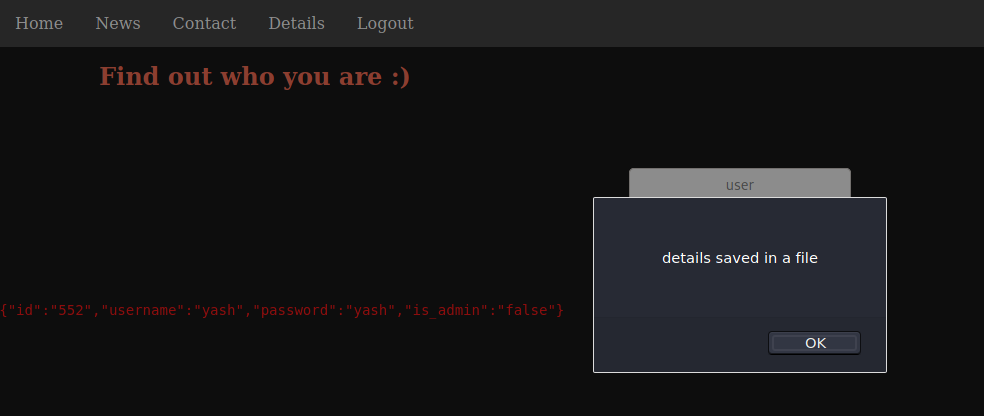
Privilege Escalation to files
Privilege Escalation to yash
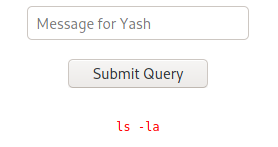
Escalation to root
PreviousContainMe (html path command injection + SUID privesc+lateral to container with ssh + mysql privesc)NextVulnNet-Internal (SMB/NFS/Rsync exploit + TeamCity Privesc)
Last updated